2024-10-22 –, Europe - Main Room
This presentation explores my discovery of unconventional malware persistence techniques through registry modifications and DLL hijacking vulnerabilities. We'll delve into cases involving Windows Internet Explorer, Win32API cryptographic features, Windows Troubleshooting, Microsoft Teams (patched), and Process Hacker 2 (patched in v3). The research highlights the exploitation of legitimate Windows resources for persistence and compares these methods with traditional techniques employed by APT groups and ransomware authors.
This presentation explores my discovery of unconventional malware persistence techniques through registry modifications and DLL hijacking vulnerabilities. We'll delve into cases involving Windows Internet Explorer, Win32API cryptographic features, Windows Troubleshooting, Microsoft Teams (patched), and Process Hacker 2 (patched in v3). The research highlights the exploitation of legitimate Windows resources for persistence and compares these methods with traditional techniques employed by APT groups and ransomware authors.
Detailed Proposal:
What is Malware Persistence?
An introduction to malware persistence, explaining how it allows malicious software to maintain a foothold on a compromised system.
User Privileged Techniques:
Exploring persistence methods that require only user-level privileges, such as registry modifications and leveraging user-specific settings.
Admin Privileged Techniques:
Investigating persistence techniques that need administrative privileges, including advanced registry modifications and system-level changes.
WinAPI Cryptography Features for Persistence:
Analyzing how Windows cryptographic APIs can be misused for maintaining persistence.
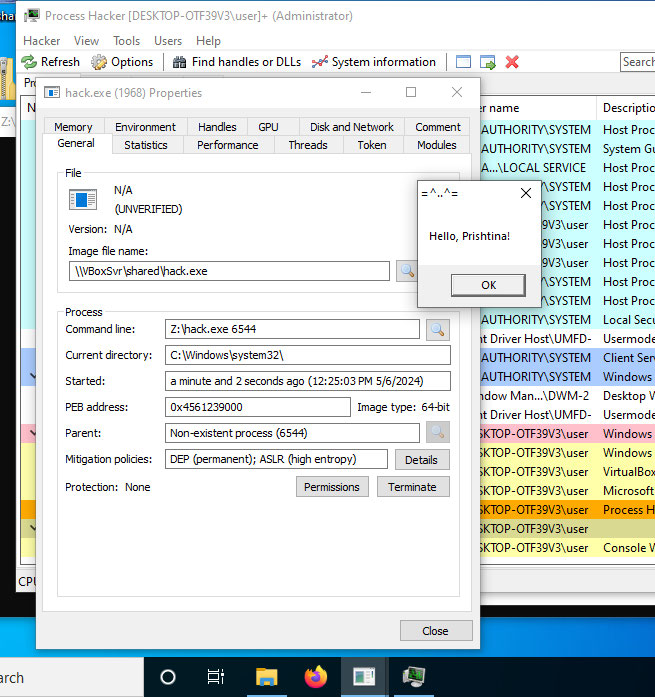
Vulnerability in Process Hacker 2:
A case study on exploiting a vulnerability in Process Hacker 2 for persistence, and the subsequent fix in Process Hacker 3.
Using Legitimate URLs for Bypassing and Persistence:
Examining the use of legitimate URLs and online services to bypass detection and maintain persistence.
Hunting for Persistence: From Zero to Hero:
A practical guide on hunting for and identifying new persistence techniques, with step-by-step methodologies and real-world examples.
Comparison with Classical Techniques:
Comparing these new methods with classical persistence techniques used by APT groups and ransomware authors, highlighting their effectiveness and stealthiness.
Explore the integration of machine learning models to predict and identify new persistence techniques. Investigate the potential for automated malware persistence using AI to adapt to and evade AV/EDR solutions dynamically.
Cybersecurity enthusiast, author, speaker and mathematician. Author of popular books:
MD MZ Malware Development book (2022)
MALWILD: Malware in the Wild book (2023)
Author and tech reviewer at Packt
Author of Malware Development for Ethical Hackers book by Packt (2024)
Co founder of MSSP Research LAB, author of many cybersecurity blogs, HVCK magazine
Malpedia contributor
Speaker at BlackHat, DEFCON, Security BSides, Arab Security Conference, Hack.lu, Standoff, etc conferences